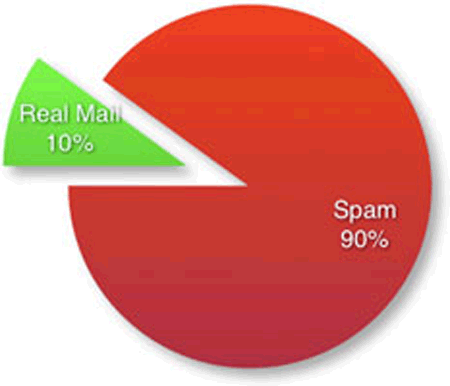
As far back as January 2013 the New York Times ran a story about Chinese hackers who successfully installed 45 malicious-ware items on the NYT’s network with Symantec’s antivirus detecting just one of them. It’s a common story. Recently we seen a computer with Trend Micro Titanium edition installed that had around 90 malware items and Trend did not detect a single one of them. You can read more about this in my other posts about computer security and why your annual investment in antivirus and firewalls will be giving you a false sense of safety.
In 2013 Symantec (Norton) would not comment on the Chinese hacking story, but in this article they fessed up and said antivirus is not enough to face today’s threats. In our experience in the trenches no antivirus is up to the task, regardless of who wins what award for best AV of the year in computer magazines. The no virus found message after a 2 hour scan is certainly one of the problems in creating a false sense of security.
Modern malware has also shown the ability to interact with antivirus and take control of these programs. So far the security industry response has been to keep their customers spending and installing antivirus. It’s about as lame as the response to hackers at ATM’s – use your left hand to hide your PIN, and while we are at it let’s introduce tap & go cards.
Until things change (and don’t expect that anytime soon) you are going to need to be aware of the warning signs of a compromised system. Trojans, viruses, malware and spyware are programs that can infect systems with no user interaction on vulnerable, exploited systems. Sometimes you will see pop ups or fake antivirus, other malware is less obvious. What is a vulnerable system? Typically small business and home/home office computers that only have an AV installed, with no other levels of security hardening.
Typical warning indicators or group of indicators of malware infection:
1. You have a downloaded a free antivirus program and it instantly found a lot of viruses and opens the scan window every time you start your computer. The search term “free antivirus” and other search terms like speed up my computer or registry cleaner program are common infection methods.
2. Your existing antivirus program has alerted you to a scan with a result, but failed to delete or quarantine the found items, or your AV has shut down.
3. Your computer is running slower than normal, crashes programs or restarts randomly.
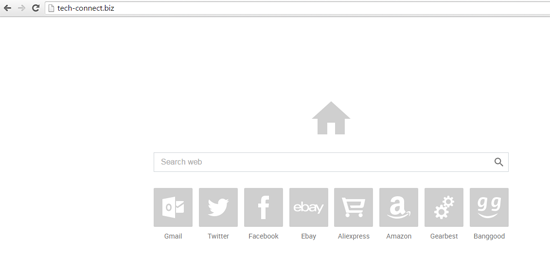
4. Your browsers start page has changed, and, or your searches redirect you to pages you didn’t search for.
5. The internet has slowed down and generally the computer is running much slower.
**You still need to have an antivirus installed for the viruses it catches, and for banking compliance on websites.
There are a number of levels to hardening your computer beyond an antivirus program. If you are in Perth WA contact us for optimised security, screening for bugs, and current best practice hardening.
Want to know which is the best AV at this time? The free Microsoft Security Essentials is our preference but stopped working on XP as of April 8 this year. If you have trouble with Windows 7 backup and MSE you may need to uninstall and install an alternative.