One of our clients was not receiving any emails in Hotmail or Outlook.com if the email contained any reference to banking or the financial running of his business here in Perth Western Australia. He had contacted hotmail help desk who were unable or unwilling to resolve the issue.
Here is how the scam worked.
- emails sent to the client were being siphoned off if they contained invoices, bank details, BSB numbers – just about anything to do with the financial running of the business.
- the missing emails were then used to instruct the sender to note a change of banking details. A new BSB and Acct number was issued for a new account at the ANZ bank. This bank was here in Australia and any payments to this account were no doubt forwarded to another bank account in a foreign country.
- any emails with baking related information, remittance advice, etc would never arrive in our clients inbox.
We were able to locate all the missing and forwarded emails, track down the email address of the thief and prevent any further access to the account. By now we had discovered the bank (ANZ), and with absolute certainty the method used to hack our clients passwords through hotmail. The client then had some information to hand over to the federal police.
If you are facing a similar situation don’t delay, contact us today to help you resolve this issue.
]]>
Microsoft is ending support for the junk spam filter known as Smartscreen technology. At a time when email spam and phishing emails are at an all time high why is Microsoft ending support for Smartscreen? It’s worked well over the years because of the Bayesian technology and when your inbox starts getting 100 spam emails a day you are going to wonder how you are going to live without it. User trends such as cloud based computing is driving the change to Exchange Online Protection and ATP Advanced Threat Protection.
For those who do not use Office 365, Sharepoint, or Exchange Online, some ISP’s have some type of spam protection, others don’t. Some ISP’s will no doubt start charging (as one notable ISP has been doing for years with poor results if their forums are a gauge of spam filtering success or failure). Small business with their own domain name will probably have spam protection but it will need to be enabled, computers configured to work with the filter, and some basic education for end users.
Here are a few basic tips to help you avoid being seen as a live candidate and get on email spam lists:
- don’t open an email that is obvious spam
- don’t reply to a spammer to abuse them
- don’t delete email, this action is likely to send a signal that you are live. Sending an email to spam folder does not send this signal.
- don’t use your own email on forums and for sale sites, get a throwaway email address
- report unwanted (spam) email from your local liquor store or real estate to ACMA.com.au to help discourage our sacred inbox becoming a marketing portal.
- have an anti spam software solution in place
Don’t put up with spam every day. It uses bandwidth and is a complete waste of time and makes people angry. We provide an easy support solution via remote access to log in to your computer and configure for both home and small business, home office etc. There is a basic one hour charge to configure antispam measures which is better than dealing with spam everyday.
]]>
emails accounts like gmail are used by small business and professionals as a quick and easy (free) email service but there’s a catch. If you get hacked there’s no one to call, you are out in the cold and left to your own resources.
Hacking is mostly not really about hacking, but guessing your password. We see passwords all the time that look like this:
abc1234
password
and so on. If you are running a business off this free email system you should be prepared for a disaster or you might never see your email again.
To mitigate the risk:
- associate a mobile phone number with your account
- if you are trying to regain access to a lost or hacked account it seems you should be doing this from the same computer you usually log in with, otherwise flags are raised and it will be more difficult.
- setup a secondary email address in your account, though if your account is hacked this might be changed.
- set up strong passwords, not the name of your cat you talk about on your social profiles.
You can also setup gmail to use offline so if you do get hacked you will have access to old emails. Follow the steps in this support article.
https://support.google.com/mail/answer/1306849?hl=en
]]>
You will know it if you have a browser redirect virus, also known as the google redirect virus or malware. The various iterations of the dreaded browser hijack or redirect removal solution is a mystery to many on internet forums. It’s nasty and resists every attempt at removal. It is invisble, undetectable by all the malware scanners and antivirus programs including Norton’s Powerful Eraser tool, bitdefender speciality tools, eset’s usually very efficient scanner in ramdisk, in fact just about everything.
We had a business client with this infection and after struggling to remove it, we decided to persevere until we found the mechanism and methods to remove it. Unfortunately, it seems each variant or type of this infection has it own methods to provide a successful removal. There is no single access point to remove it.
But good news! We offer an online (remote access) service to remove this, along with all the other bugs on your computer. If you are anywhere in Australia call or email to arrange a good time for us to log in for you.
www.wiredoffice.com.au has been providing trusted service for over 15 years and is a Microsoft registered partner, and a Microsoft Certified Professional (MCP).
]]>In 2013 Symantec (Norton) would not comment on the Chinese hacking story, but in this article they fessed up and said antivirus is not enough to face today’s threats. In our experience in the trenches no antivirus is up to the task, regardless of who wins what award for best AV of the year in computer magazines. The no virus found message after a 2 hour scan is certainly one of the problems in creating a false sense of security.
Modern malware has also shown the ability to interact with antivirus and take control of these programs. So far the security industry response has been to keep their customers spending and installing antivirus. It’s about as lame as the response to hackers at ATM’s – use your left hand to hide your PIN, and while we are at it let’s introduce tap & go cards.
Until things change (and don’t expect that anytime soon) you are going to need to be aware of the warning signs of a compromised system. Trojans, viruses, malware and spyware are programs that can infect systems with no user interaction on vulnerable, exploited systems. Sometimes you will see pop ups or fake antivirus, other malware is less obvious. What is a vulnerable system? Typically small business and home/home office computers that only have an AV installed, with no other levels of security hardening.
Typical warning indicators or group of indicators of malware infection:
1. You have a downloaded a free antivirus program and it instantly found a lot of viruses and opens the scan window every time you start your computer. The search term “free antivirus” and other search terms like speed up my computer or registry cleaner program are common infection methods.
2. Your existing antivirus program has alerted you to a scan with a result, but failed to delete or quarantine the found items, or your AV has shut down.
3. Your computer is running slower than normal, crashes programs or restarts randomly.
4. Your browsers start page has changed, and, or your searches redirect you to pages you didn’t search for.
5. The internet has slowed down and generally the computer is running much slower.
**You still need to have an antivirus installed for the viruses it catches, and for banking compliance on websites.
There are a number of levels to hardening your computer beyond an antivirus program. If you are in Perth WA contact us for optimised security, screening for bugs, and current best practice hardening.
Want to know which is the best AV at this time? The free Microsoft Security Essentials is our preference but stopped working on XP as of April 8 this year. If you have trouble with Windows 7 backup and MSE you may need to uninstall and install an alternative.
]]>So what’s the danger of a text file with no ability to run a program (executable)? A cookie can contain information useful to an attacker to enable the computer to be re-infected when the original virus infection is removed. Being an insecure text file cookies can easily be harvested by malicious programs. When a virus or backdoor trojan infects a computer it will install a malicious cookie, in part to facilitate re-infection in the future, particularly if the user visits one of the websites where the original infection came from.
Virus analysts have also identified exploits in common browsers where information can be harvested from cookies to gather login information to various websites the customer is using.
Currently, the best antivirus program that scans for and removes malicious text files such as cookies is Bitdefender. You can download a copy here.
]]>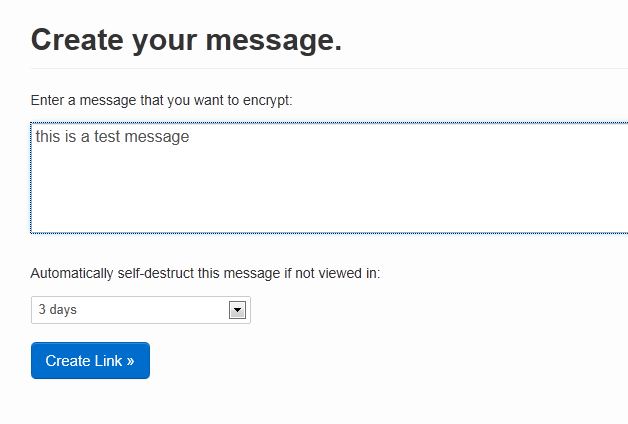 Sending someone an email with sensitive information such as your credit card number, passwords, or other information can leave that message hanging around in email folders, instant messaging programs or texts for a period of time until it’s deleted, and even then can be recoverable.
Sending someone an email with sensitive information such as your credit card number, passwords, or other information can leave that message hanging around in email folders, instant messaging programs or texts for a period of time until it’s deleted, and even then can be recoverable.
Enter the burn after reading solution from Oneshar. This is the stuff of a James bond movie. The initial data you send in the message is encrypted, once read the message self destructs, and if your intended reader does not read the message it will self destruct after the time allocated by you. By default this is 3 days.
I can see a lot of uses for this. It’s free and you can get it here.
]]>We see the failure of electro-mechanical hard drives on an almost daily basis. These clumsy but delicate devices are nearing the end of their technology life and SSD (solid state drives) with large capacity and mainstream pricing will take their place. The end-of-life for these troublesome drives is welcomed, though I must point out that while everyone moans about the unreliability of IDE and SATA drives, they are built to a price and you got what you asked for. Some drives seem to be a little more reliable than others, while the WD Velociraptor is very reliable, at a price.
We would expect to see data retained when the flash drive has reached its write cycle and this presents its own security issues for enterprise, medical, and all other users where critical data is stored. Researchers at the non-volatile-systems -laboratory found that commercial erasing programs were not entirely affective with data remnants still available to testers.
A SSD drive that is unmountable or no longer appears to be working may be mistakenly discarded with accessible data on it.
]]>